Although it may not be useful to most unless you are using the OpenAthens with Shibboleth IdP, I though running through some SAML request debugging which shows how you can take apart a SAML request, rewrite it and then re-encode it to assist in debugging or testing.
The purpose of this was to test the SAML attributes that were being exposed to sP (service providers) from our new OpenAthens deployment to verify it was working as expected.
Essentially you’re going through the process of:
- Initial request
- Decode the URL
- Decode the XML
- Change the XML (to include your new IdP)
- Encode the XML
- Encode the URL
- Make the request (with the modified SAML request)
- Output
Performing the Tests
Open an incognito or private browser window.
Open the Developer Tools, and go to the “network” tab so you are able to see each of the resources (and requests) that are being made.
The open Athens IdP Endpoint is at the link: https://login.openathens.net/saml/2/sso/domain.com
The new prefix for the modified SAML requests: https://login.openathens.net/saml/2/sso/domain.com/c/ukfed?SAMLRequest=
Note that i’m hiding the our real IdP name, so using the fake one: idp.domain.com, so you’d need to substitute in your own.
Initial Request
First open this page https://login.openathens.net/resources/static/ssodebug.html
Click the OpenAthens SSO Debug button

This will set the OpenAthens logon page into Debug Mode, what this means is you’ll see a splash page displaying debug information such as the attribtues that your IdP has released to OpenAthens so you can check what they are.
Then open a new tab and go to the UK federation test SP https://www.ukfederation.org.uk/content/Documents/TestSPHome
Note that you need to be part of the UK Federation, you’ll also need to have statically configured the sP within OpenAthens so you can send requests to that directly.
Click the link shown in the box https://test.ukfederation.org.uk/Shibboleth.sso/SeamlessAccess
From the list start typing your organisation name, then click on it to take you to your current IdP login, in our example this is Shibboleth IdP which is being retired in favour of OpenAthens backed by OKTA to provide the directory information.
At the Shibboleth IdP, don’t log in, instead look into the Developer Tools window, specifically the “Network” tab.

Then a few parts of the output need to be removed.
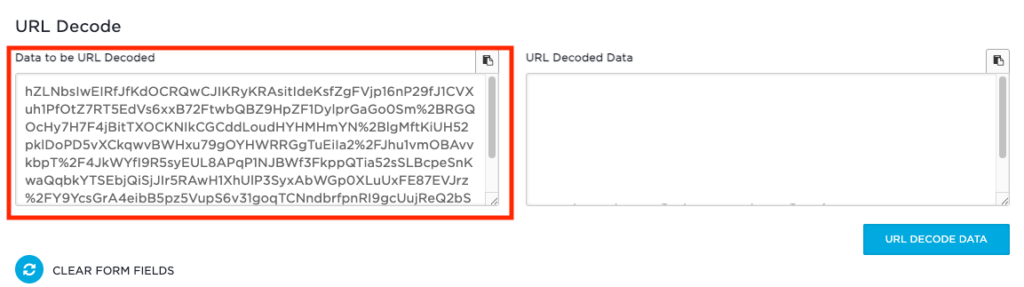
https://idp.domain.com/idp/profile/SAML2/Redirect/SSO?SAMLRequest=hZLNbsIwEIRfJfKdOCRQwCJIKRyKRAsitIdeKsfZgFVjp16nP29fJ1CVXuh1PfOtZ7RT5EdVs6xxB72FtwbQBZ9HpZF1DylprGaGo0Sm%2BRGQOcHy7H7F4jBitTXOCKNIkCGCddLoudHYHMHmYN%2BlgMftKiUH52pklDoPD5vXCkqwvBWHxu79gOYHWRRGgTuEiIa2%2FJhu1vmOBAvvkbpT%2F4JkWYfI9R5syEUL8APqP1NJBWf3FkppQTia52sSLBcpeSnKwaQqbkYTSEbjQiSjJIr5RAwH1XhUlP3SyxAbWGp0XLuUxFE87EVJrz%2FY9YcsGrA4eibB5pz5VupS6v31goqTCNndbrfpnRI9gcUujReQ2bStmXWL7UXx17H8p20y%2B7db0E66rym92HNaWrMHD14uNkZJ8RVkSpmPuQXuICV9Qmcny9%2FTmH0D&RelayState=cookie%3A1741964658_547cRemove from the beginning:
https://idp.domain.com/idp/profile/SAML2/Redirect/SSO?SAMLRequest=Remove from the end:
&RelayState=cookie%3A1741964658_547c
So it looks like this:
hZLNbsIwEIRfJfKdOCRQwCJIKRyKRAsitIdeKsfZgFVjp16nP29fJ1CVXuh1PfOtZ7RT5EdVs6xxB72FtwbQBZ9HpZF1DylprGaGo0Sm%2BRGQOcHy7H7F4jBitTXOCKNIkCGCddLoudHYHMHmYN%2BlgMftKiUH52pklDoPD5vXCkqwvBWHxu79gOYHWRRGgTuEiIa2%2FJhu1vmOBAvvkbpT%2F4JkWYfI9R5syEUL8APqP1NJBWf3FkppQTia52sSLBcpeSnKwaQqbkYTSEbjQiSjJIr5RAwH1XhUlP3SyxAbWGp0XLuUxFE87EVJrz%2FY9YcsGrA4eibB5pz5VupS6v31goqTCNndbrfpnRI9gcUujReQ2bStmXWL7UXx17H8p20y%2B7db0E66rym92HNaWrMHD14uNkZJ8RVkSpmPuQXuICV9Qmcny9%2FTmH0DDecode The URL
Then in another tab, open the page https://www.samltool.com/url.php (URL Encode/Decode) that allows you to decode the URL.
In the URL Decode box paste the above into the data to be URL decoded:
Then click the URL DECODE DATA button and the following should be outputted.
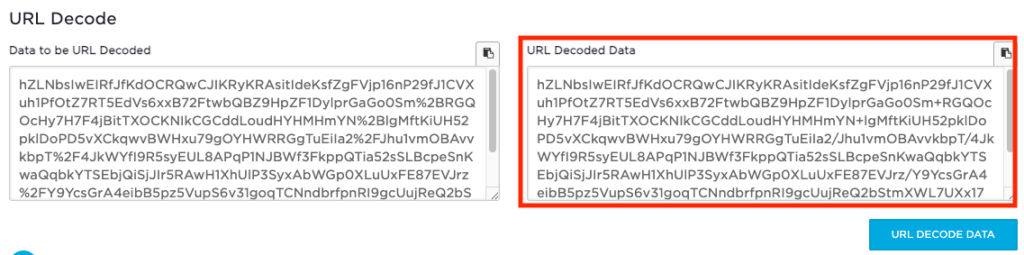
Then take the output from the right and go to the Base 64 Decode + Inflate link, paste the output into the Deflate and Encoded XML.
Decode The XML
Next go to the page https://www.samltool.com/decode.php (Base 64 Decode + Inflate).

Then click the DECODE AND INFLATE XML button and the following should be output.
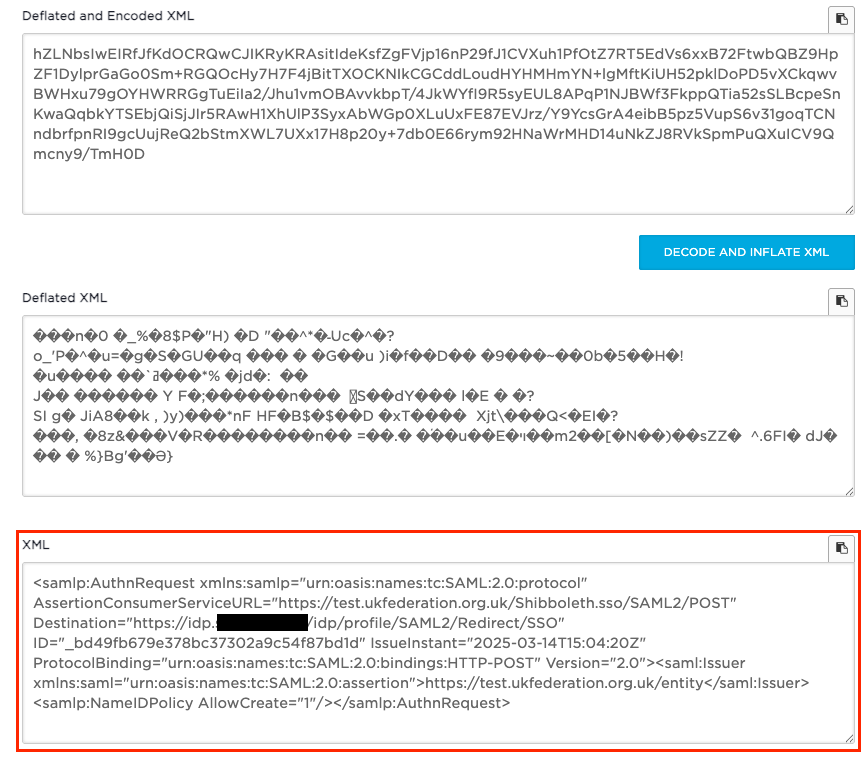
Change The XML
Take the output in the box and replace the following:
https://idp.sanger.ac.uk/idp/profile/SAML2/Redirect/SSOwith:
https://login.openathens.net/saml/2/sso/sanger.ac.uk/c/ukfedAfter the change it should look something like this:
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceURL="https://test.ukfederation.org.uk/Shibboleth.sso/SAML2/POST" Destination="https://login.openathens.net/saml/2/sso/domain.com/c/ukfed" ID="_bd49fb679e378bc37302a9c54f87bd1d" IssueInstant="2025-03-14T15:04:20Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0"><saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">https://test.ukfederation.org.uk/entity</saml:Issuer><samlp:NameIDPolicy AllowCreate="1"/></samlp:AuthnRequest>
We are rewriting the request to include the OpenAthens IdP rather than our current IdP to allow us to perform a test.
Encode The XML
The click the link https://www.samltool.com/encode.php (Deflate + Base64 Encode), now you need to paste in your altered XML from the previous step.

Then click the DEFLATE AND ENCODE XML, which should output the following:
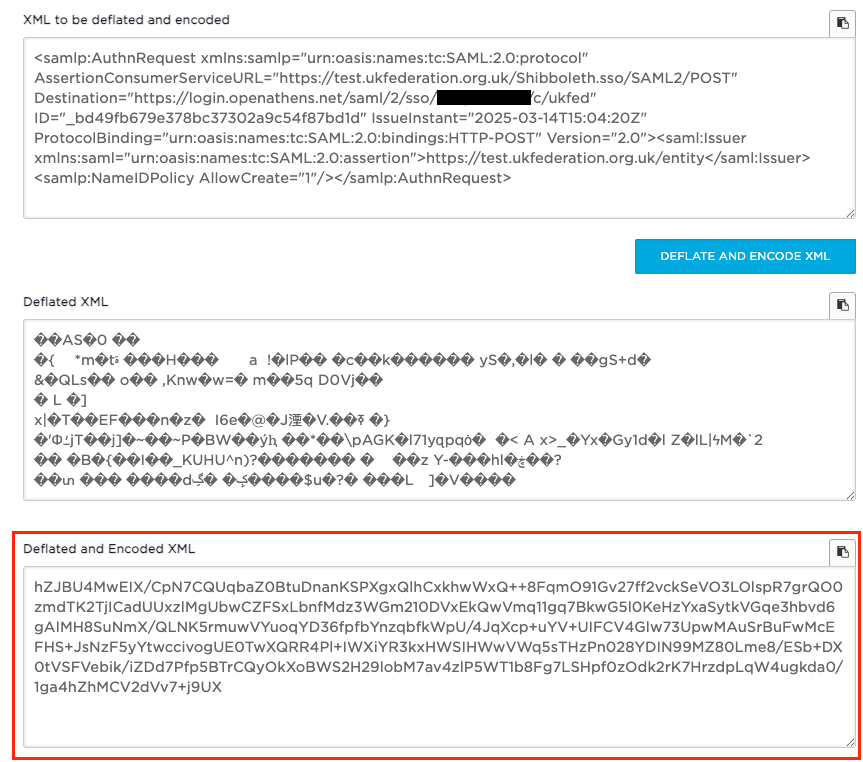
Encode The URL
Next we need to go to the link https://www.samltool.com/url.php (URL Encode/Decode) again, but this time we’ll be encoding the data, rather than decoding which we did earlier.
Paste the above text into the URL Encode box:
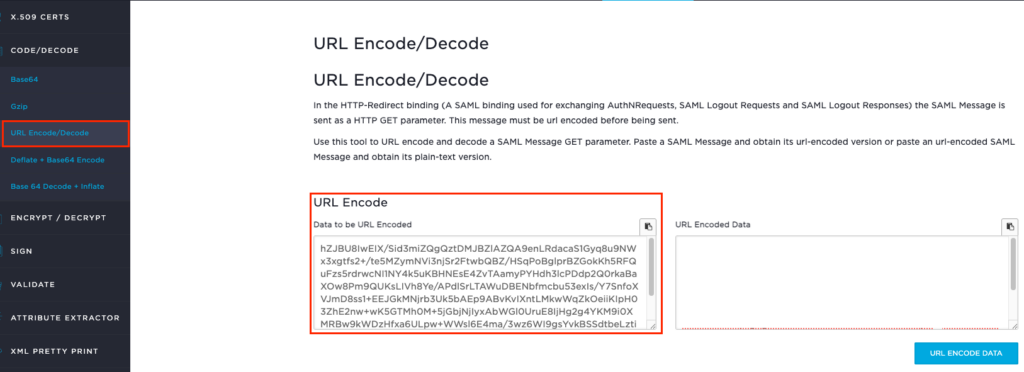
Click the URL ENCODE DATA button.
After this has been processed you have your encoded output:
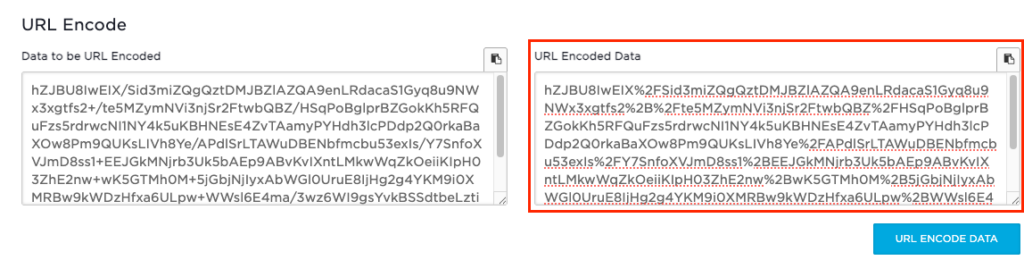
Make The Request
Copy the output and then create the following URL by taking the following:
https://login.openathens.net/saml/2/sso/domain.com/c/ukfed?SAMLRequest=Append encoded XML to it to create the following URL:
ttps://login.openathens.net/saml/2/sso/domain.com/c/ukfed?SAMLRequest=hZJBU8IwEIX%2FSid3miZQgQztDMJBZlAZQA9enLRdacaS1Gyq8u9NWx3xgtfs2%2B%2Fte5MZymNVi3njSr2FtwbQBZ%2FHSqPoBglprBZGokKh5RFQuFzs5rdrwcNI1NY4k5uKBHNEsE4ZvTAamyPYHdh3lcPDdp2Q0rkaBaXOw8Pm9QUKsLIVh8Ye%2FAPdlSrLTAWuDBENbfmcbu53exIs%2FY7SnfoXVJmD8ss1%2BEEJGkMNjrb3Uk5bAEp9ABvKvIXntLMkwWqZkOeiiKIpH03ZhE2nw%2BwK5GTMh0M%2B5jGbjNjIyxAbWGl0UruE8IjHg2g4YKM9i0XMRBw9kWDzHfxa6ULpw%2BWWsl6E4ma%2F3wz6WI9gsYvkBSSdtbeLztietX8ZK38qJ%2Bm%2FBYN2yp1m9MynN63FnQevlhtTqfwUzKvKfCwsSAcJYYSm%2Fcrf%2F5F%2BAQ%3D%3DOpen a new browser tab, paste in your edited URL and it should now open the OKTA login page.
Sign in and once signed in, the following should be displayed.
Output
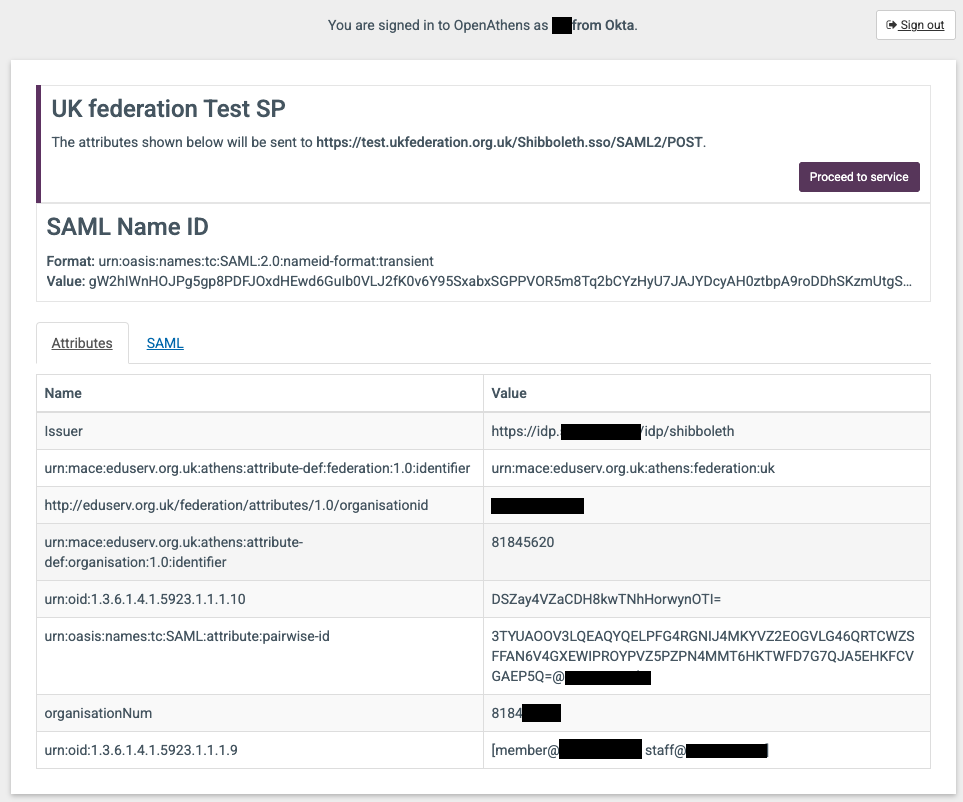
The output show the attributes that are going to be passed to the application from OpenAthens.
If you don’t see the above page then you may not have enabled the SSO debug using the link in Fig A above.
If you were to click “Proceed to service” you’d get an error saying that the request signature is invalid, this is because you’ve tampered with the request en-route, but we don’t need to proceed to the service, its the output of this debug screen we are interested in.