A plugin has been developed to allow the monitoring of the status of VPN Tunnels on the Palo Alto Firewall.
The script uses the Palo Alto Firewall API to access the relevant part of the API “tree” to find the status of the VPN Tunnel(s).
You can find the current version of the plugin here:
https://github.com/tristanhself/general/blob/master/check_pa_vpn_status.py
Using the script is fairly straightforward, you will need to have a suitable API key to give access to the Palo Alto Firewall API, then you’ll need to determine the name of the IPSec VPN Tunnel you wish to monitor.
Authentication
You first need to retrieve an API key, you may also need to create a special read only account for this purpose too.
Determine Tunnel Name
You’ll need to find the Tunnel Name you wish to monitor, you can do this from within the Palo Alto Firewall web interface Network → IPSec Tunnels, then find the tunnel by the name:
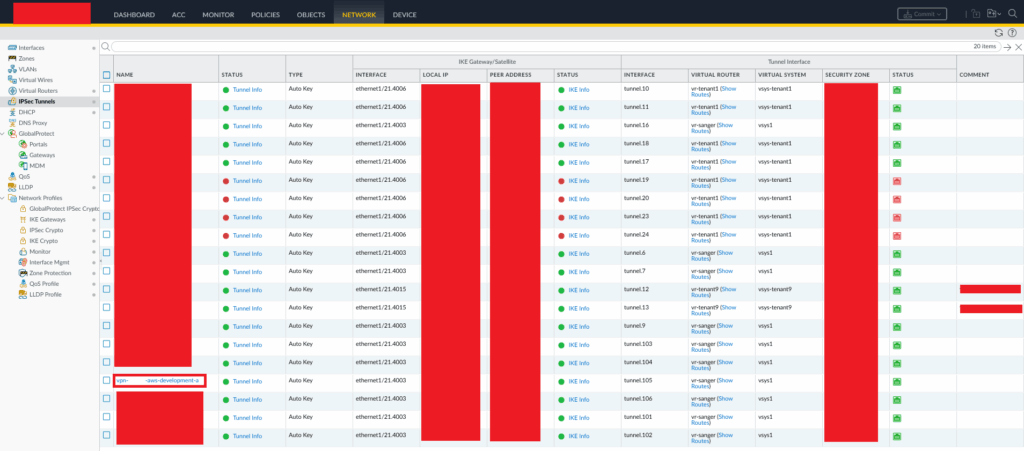
Highlighted is an example IPSec VPN Tunnel name we wish to use, we’ll use this when it comes to demostrating the usage of the script, and its output.
Using the Script
To use the script, you’ll need to pass in some arguments at runtime. If you are calling the script from a monitoring software like NagiosXI, specify these within your “command” and argumentise the input values into $ARG1$, $ARG2$ and $ARG3$ for the URL, API Token and Tunnel Name respectively.
./check_pa_vpn_status.py -e <URL to Firewall including /api> -a "<API Token>" -t <Tunnel Name>With some real inputs:
./check_pa_vpn_status.py -e https://firewall1.domain.com/api -a "<Secret API Key>" -t vpn-tunnel-aWe’ll get an example output such as the following depending on if the IPSec VPN Tunnel is up or down:
OK - IPSec VPN UP - vpn-tunnel-a tunnel.103 18.35.26.142.
CRITICAL - IPSec VPN DOWN - vpn-tunnel-a tunnel.103 18.26.57.32If you enter an invalid tunnel name, API URL etc, the script will return UNKNOWN.
Additional Information
- https://helpdesk.paessler.com/en/support/solutions/articles/76000067482-palo-alto-network-vpn-monitoring-powershell-script
- https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/enable-api-access
- https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/get-your-api-key
- https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/authenticate-your-api-requests
- https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/make-your-first-api-call
- https://docs.paloaltonetworks.com/pan-os/11-0/pan-os-panorama-api/get-started-with-the-pan-os-xml-api/explore-the-api
