Although its becoming increasingly rare nowadays to be using un-encrypted connections, let’s see what it really means at the network level. Un-encrypted connections on their own are not necessarily a problem, its all about what value what you are sending has and therefore what could be exposed to a nefarious actor.
If you are viewing the weather information from a public website does it matter if this content is un-encrypted? probably not its not of any value, what would a hacker gain by reading this content, which they could just get themselves!
But taking another example, what if you were logging onto that same website with a username and password to get the weather information, would you want that username and password exposed? Maybe, maybe not, what if you’ve used that same username and password on another website, you don’t right? :), perhaps a website you’re more concerned about?
All Clear?
This week I was showing other engineers what un-encrypted really means in practice, sure this is a simple demonstration and requires the network traffic from the monitored machine to be intercepted physically, via a spanned/mirrored switch port; but you can clearly see the implications, think if you were sending traffic un-encrypted on a wireless link in a coffee shop, or worse if it was an evil twin!
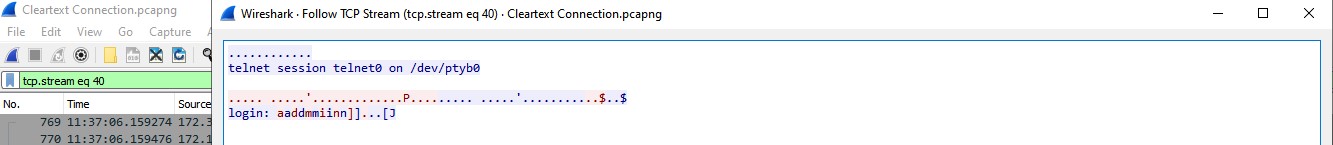
I challenged an engineer to use an un-encrypted protocol e.g. Telnet to attempt to login to a switch, of course they were told not to use their real credentials, I just wanted them to use a password/phrase and i’d be able to tell them what they typed without seeing it directly.
Using Wireshark the packet capture was taken, and well its quite clear what the passwords used were: “mypassword” and “cheese”.

Conclusion
So, what can people really see? Well everything, it means its completely “cleartext”, sure it might be mixed up with control characters and/or split across many packets, but the information is there and available for anyone who has access to the packets to read.
So, ensure you use protocols that are encrypted and when using a website where you need to log in ensure you’re seeing the “padlock” so you’re using HTTPS which is encrypted and not HTTP which is not and especially when you’re on a public or un-trusted network.